Access reviews
Regularly monitor access in the organization. Ensure each identity has only the minimal but necessary permissions.

Full control over access
PASK allows you to create a variety of review scenarios, from quick confirmation of expiration dates, through access extensions, to full access reviews based on data reconciliation. The solution supports operational security and regulatory compliance, including the DORA Regulation, by ensuring control over permissions at every stage of the identity lifecycle.
Advantages of using reviews
Reducing unauthorized access
Quickly detect redundant, outdated, or risky permissions
Flexibility
Reviews tailored to different business goals and scenarios
Change audit
Full decision history and regulatory compliance
How does access review work?
Define the goal, define the scope, and assign responsibilities - the system will handle the rest. This process allows you to align the goal and course of action after making a decision with the security policy and organizational realities.
Review's goal
The first step is to define the business goal. The PASK system allows you to precisely define the type of verification to be performed:
- modification of expiration dates
- confirmation of accesses
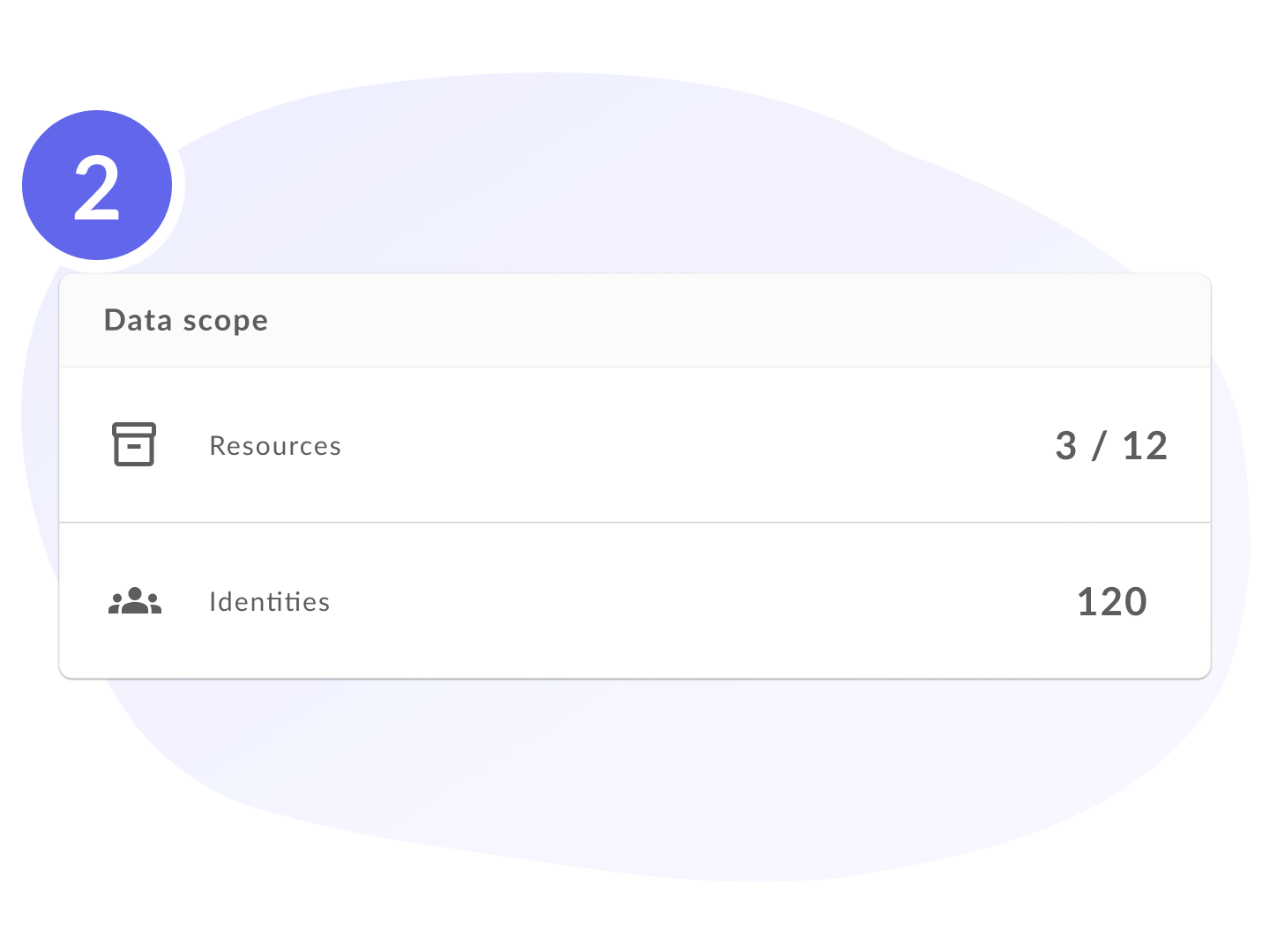
Scope of access and identity
Define the scope of the review based on your needs - from all active identities to selected groups or specific individuals. The system allows you to define rules to narrow the scope or specify precisely which identities and assets should be included in the review.
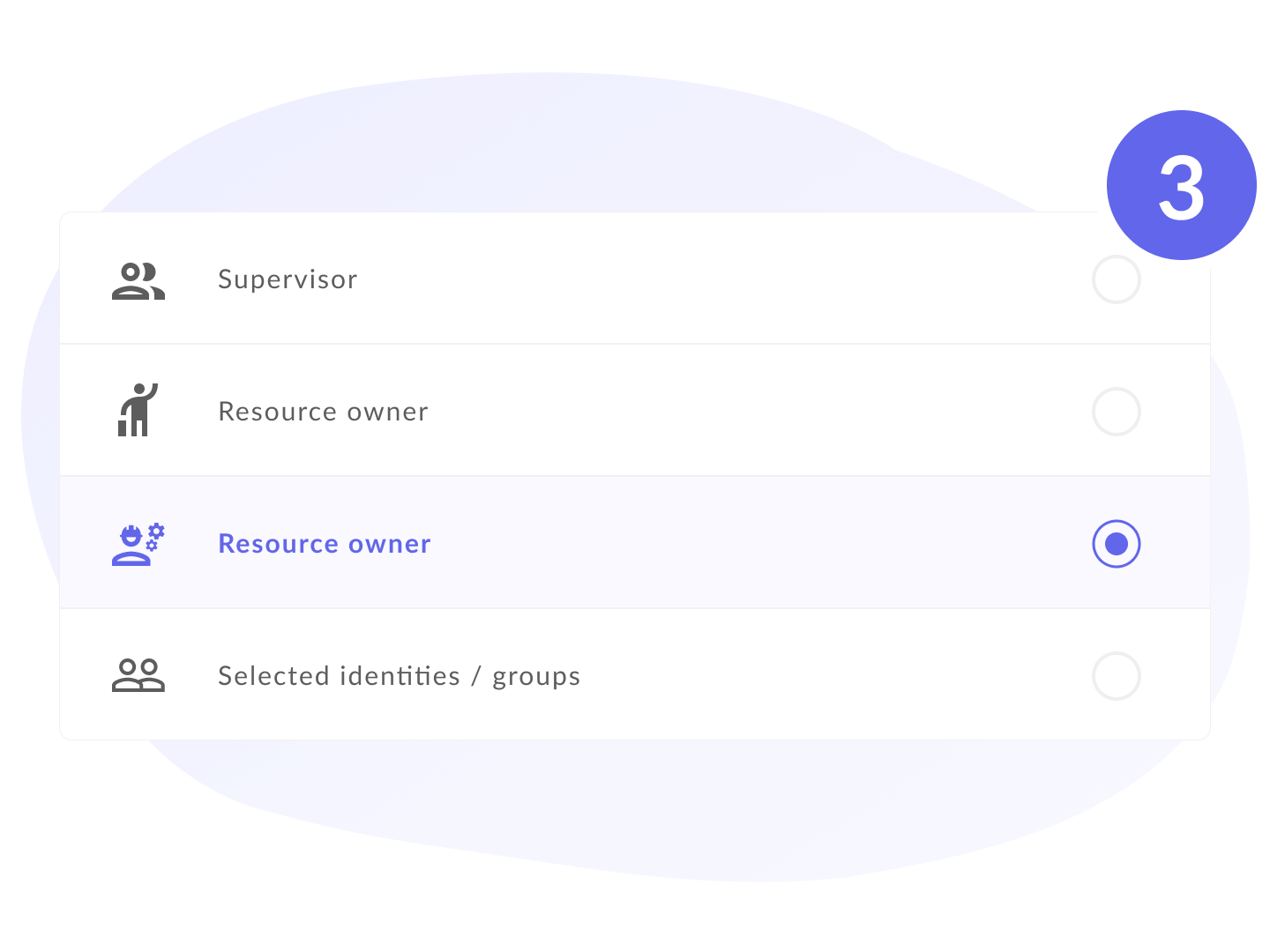
Executors
The system provides complete flexibility in defining decision-makers in the review process. You can assign decisions to superiors, resource owners/business roles, or designate specific individuals or groups. This ensures the process aligns with the organization's structure and responsibilities.
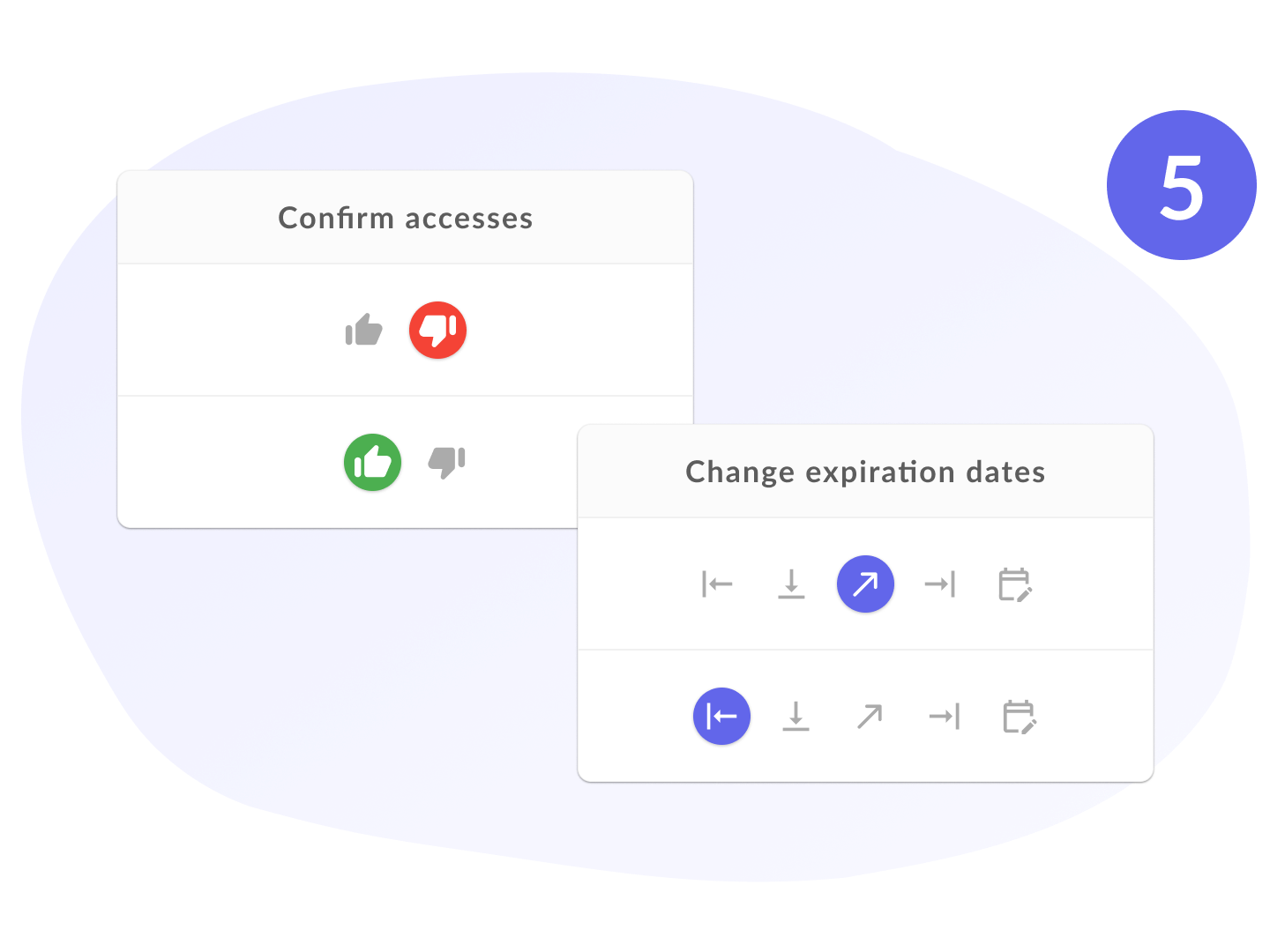
Actions after decision
Define what should happen after a decision is made – you can terminate the process at the report level, trigger execution tasks, or enable the full approval and execution process. This allows you to tailor the level of automation to your organization's policies.
Result
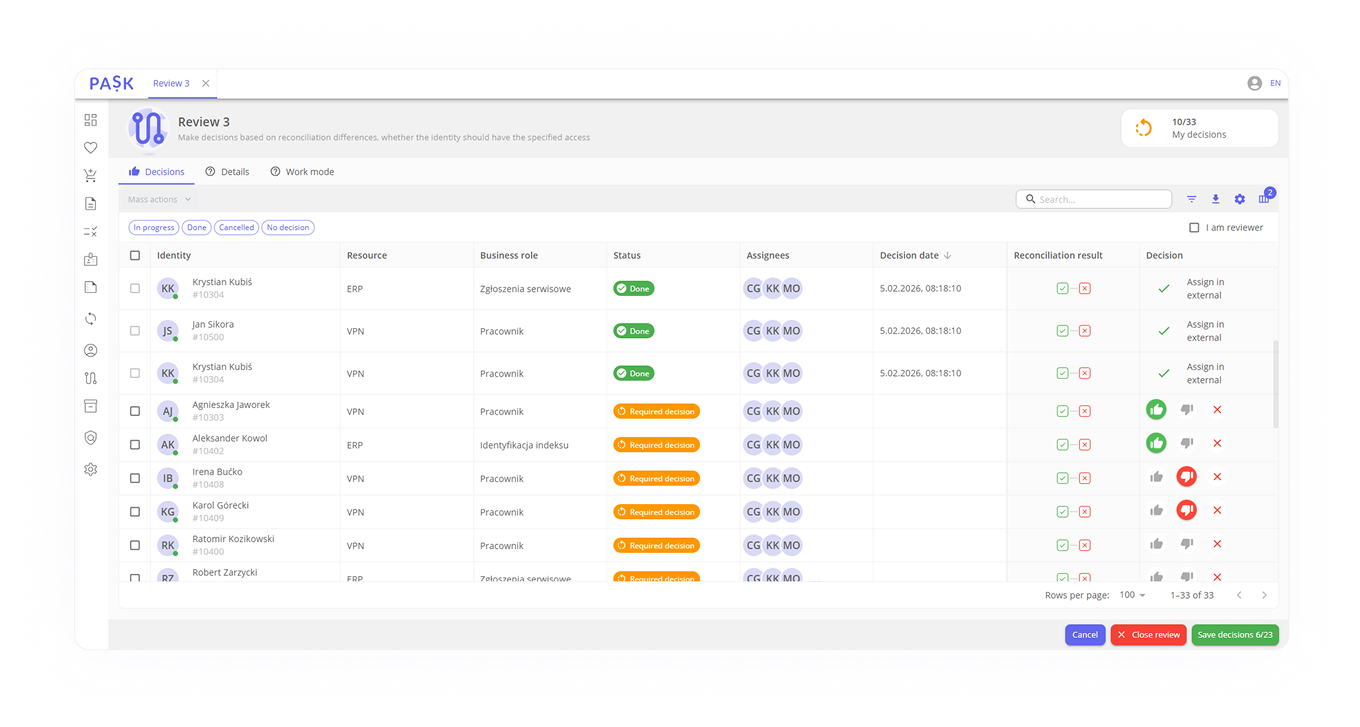
Decisions are forwarded to the appropriate executors, who conduct the review within the assigned scope. Depending on the review's purpose, various types of decisions are made, from simple (accept/reject) to more detailed (extend, shorten, or leave unchanged). This ensures the process is flexible and tailored to the business context.
Supported types of reviews
- Modification of accesses dates
- Confirmation of expiration date
- Extension of access
- Confirmation of accesses
- Confirmation of accesses (reconciliation)
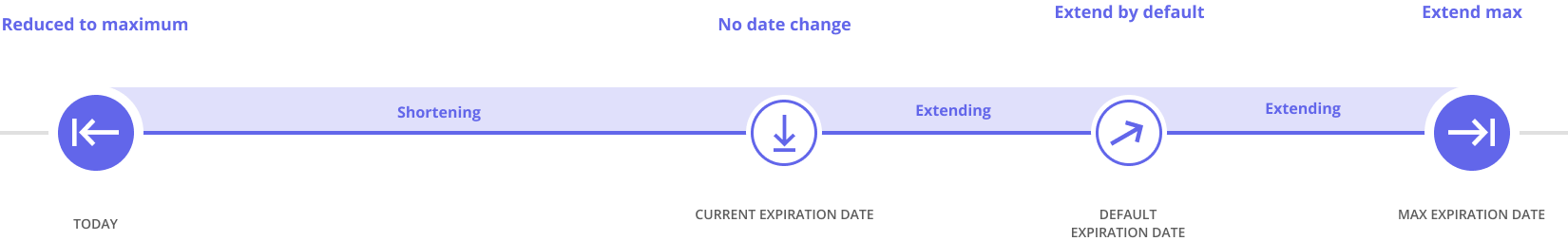
Modification of accesses dates
Easily adjust access validity periods to your current needs.
Freely change role expiration dates across the entire available range – from today to the maximum date for a given resource.
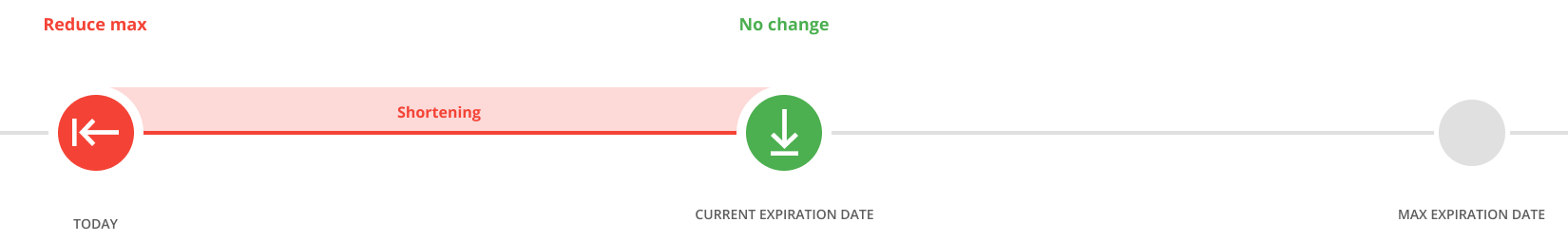
Confirmation of access expiration date
Easily check if access is valid for the duration it should be. Confirm the current date or shorten its expiration if the access information is no longer current.
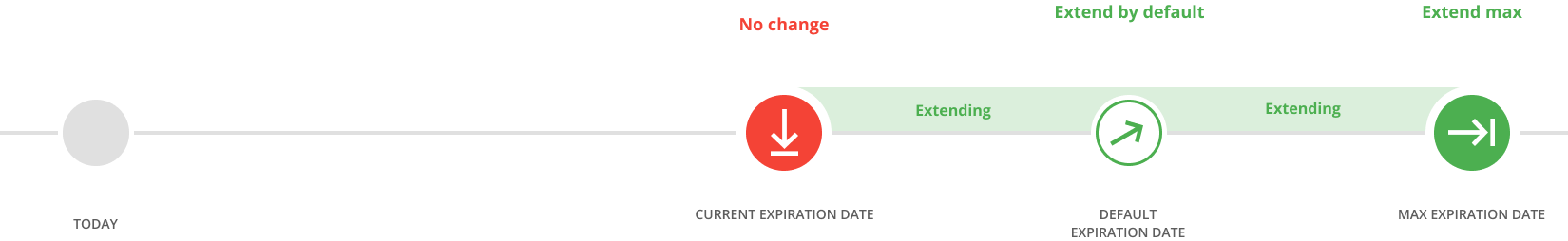
Extension of access
Extend your access in a simple and manageable way. You can keep the current date, extend it for a specific period, or set a new date as needed.
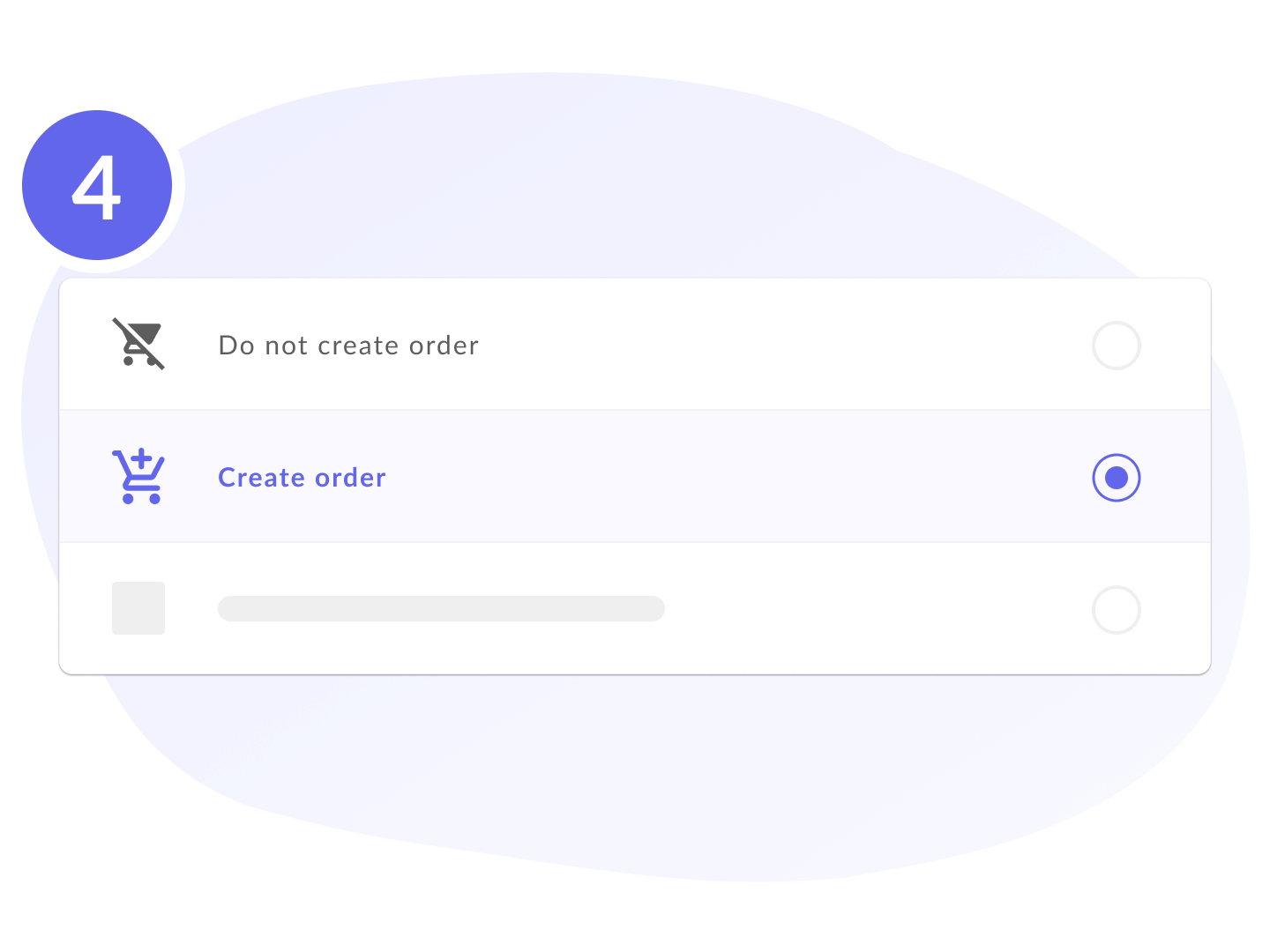
Confirmation of accesses
Ensure that users have the correct permissions.
Confirm access with a single click, and if a negative decision is made, the system can automatically issue an order to revoke access.

Confirmation of accesses (reconciliation)
Confirm accesses based on the actual status of business roles. The system helps organize permissions and ensure compliance with agreements.